Working with the Audit Log¶
To be able to access the Audit engine, you will need audit capability, set by your system administrator. Audit capability can be assigned to a read user without access to any encrypted information, in this way you can have an external auditor reviewing compliance issues etc without access to your business critical information. When the audit capability is set you will find an audit botton in your web gui. To access the audit log, push the "Audit" button in the main menu. The Audit subsystem will only be available to users who has the Audit capability. For further information see the Basic Concepts of StoredSafe.
This is the main menu of the Audit Subsystem. It will by default list all the latest audit events. To advance further in the Audit log, press the Next or Previous button at the end of the screen.
- The timestamp column will show when the event occured.
- Vault (id) column lists which (if relevant) vault and it's unique vault-id.
- Item (id) column lists which (if relevant) object and it's unique object-id.
- User 2 column list any secondary user affected, so if a user get's added to a vault, the added user will be listed as "User 2".
- Remote lists the full IPv4 or IPv6 address of the client responsible for the action that led to the audit event.
- Finally, the last column lists different event types.
Most of the events are self explanatory, however here follows a brief description on the most common events:
- DECRYPTED
An encrypted item of an object was decrypted.
- DECRYPTED NOTES
An encrypted note of an object was decrypted.
- ALARM DECRYPTED
An encrypted item of an object was decrypted and object was armed with an alert if decrypted. Alarm will be sent by syslog to a remote syslog server.
- NOTES UPDATED
A note associated with an object was updated.
- AUTH FAILURE
Failed logins, see below for further details.
- AUTH FAILURE (GPG)
The passphrase given at login was incorrect.
- AUTH FAILURE (OTP)
The system could not verify the OTP (One Time Password) sent by the Yubikey.
- AUTH FAILURE (USER)
A non-existant user was used in an login attempt.
- UPDATEUSER <id>
A system user was updated.
- VAULT UPDATED: <id>
The vault (see the vault column) was updated. Hover over the <id> field to get further details.
- VAULT DELETED: <id>
The vault (see the vault column) was deleted. Hover over the <id> field to get further details.
- REMOVEUSER FROM VAULT
A user (User 2) was removed from the vault in the Vault column.
- MOVED TO VAULT: <id>
An object was moved from one vault (See the Vault tab of the entry) to the vault ID in the event, hover with the mouse over the vault-id to see the vault name.
- COPY TO VAULT: <id>
An object was copied from one vault (See the Vault tab of the entry) to the vault ID in the event, hover with the mouse over the vault-id to see the vault name.
- MOVED TO OBJECT: <id>
An object was moved from one vault or object (See the Vault tab of the entry) to the object ID in the event, hover with the mouse over the object-id to see the object name.
- COPY TO OBJECT: <id>
An object was copied from one vault or object (See the Vault tab of the entry) to the object ID in the event, hover with the mouse over the object-id to see the object name.
- OBJECT DELETED: <id>
An object was deleted. Hover over the <id> field to get further details.
- VAULT DELETED: <id>
A vault was deleted. Hover over the <id> field to get further details.
- EDIT
The object in the Item column was edited.
- OBJECT RECREATED
All the encrypted items in the object was changed.
- LOGIN
The user logged on.
- BACKUP TRANSFER
A backup was transferred to the configured remote system.
- BACKUP COMPLETED
A backup completed successfully.
- ESCROW
Key escrow was performed, the user in the "User 2" column was given access to the vault in Vault column.
- AUDITOBJECT
An auditor performed audit on the item.
- AUDITUSER
An auditor performed audit on the user.
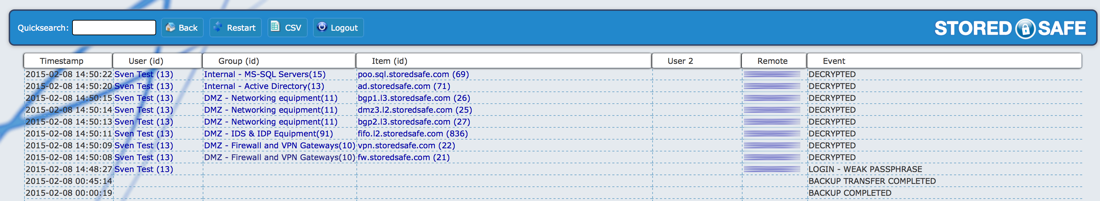
You can either type any search string in the Quick search field to search all of the audit log, an other option is to click on any click able item in the log to perform a search for it.
In the example above, we clicked on the "bgp1.l3.storedsafe.com" Item, the screen below shows the results. We can see that the object was created by the user "Sven Test" in 2012-03-10 and that the object was placed in the vault "DMZ - Networking equipment"
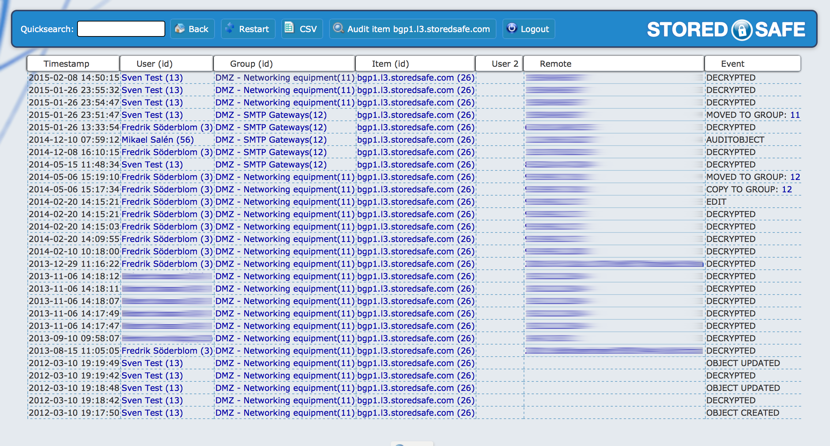
A new button as appeared on the menu above, "Audit item bgp1.l3.storedsafe.com", if we click it, we will drill down in the audit log and focus on the "bgp1.l3.storedsafe.com" item.
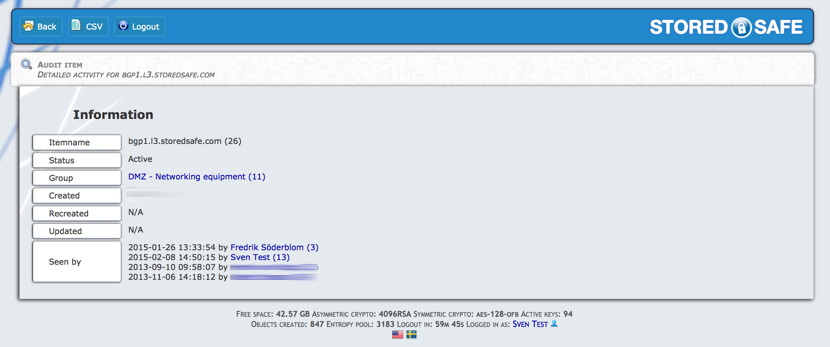
From this zoomed in view, we will be able to see meta information on the object, such as who has seen it, what vault it belongs to and if the item has been updated or not.
It's possible to cross between different audit modes within the different audit modules.
If we click on one of the users in the expanded item view of the audit log, or if we click on a user in the main menu of the audit log, we will drill down in the audit log and reveal all details about a user.
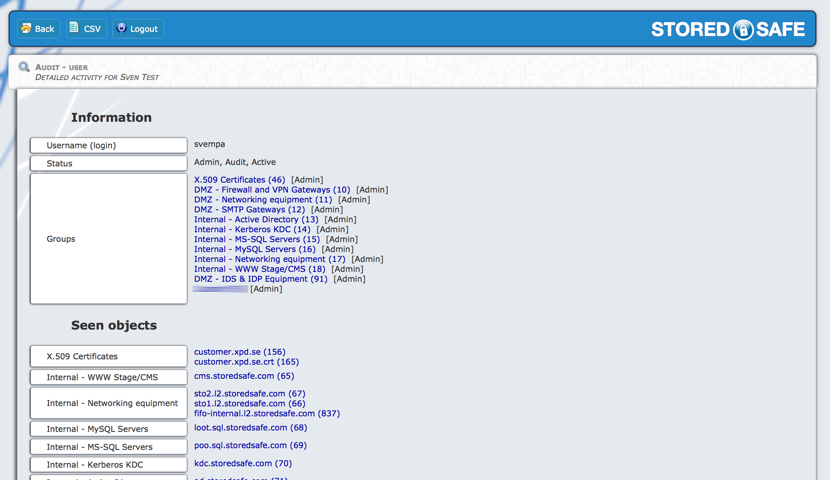
This audit information will show us all the vaults the user belongs to and what objects he has viewed.
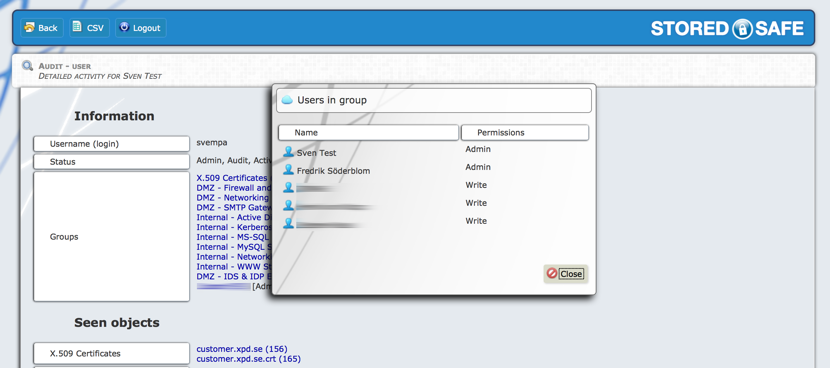
If we click on one of the vaults the user belongs to, the system will list all users, and their respective roles, in the selected vault.